Additional configuration
This page contains additional configuration for the Axiomatics Services Manager (ASM) that you may need to consider.
Disable or enable the Dashboard
Axiomatics Services Manager (ASM) offers the Dashboard functionality using an InfluxDB instance, which can be disabled or enabled depending on your needs.
- Docker deployment
- Kubernetes deployment
Disable the Dashboard
Using the console:
Navigate to the
docker/folder and stop ASM.docker-compose -f docker-compose.yml -f docker-compose.dashboard.yml downRestart ASM.
docker-compose upThis starts ASM without InfluxDB and with the Dashboard functionality disabled.
Enable the Dashboard
Using the console:
Navigate to the
docker/folder and stop ASM.docker-compose stopRestart ASM.
docker-compose -f docker-compose.yml -f docker-compose.dashboard.yml upThis starts ASM with InfluxDB and with the Dashboard functionality enabled.
Disable the Dashboard
The steps below apply both to local and cloud Kubernetes installations.
Open the
kubernetes/asmcharts/values.yamlfile and set the following:Parameter Value enableMetricsDashboardfalseUpgrade the Helm charts.
helm upgrade -n axiomatics-asm asm -f asmcharts/values.yaml asmchartsThis starts ASM without InfluxDB and with the Dashboard functionality disabled.
Enable the Dashboard
Local installation
The steps below apply to local installations using minikube.
Open the
kubernetes/asmcharts/values.yamlfile and set the following:Parameter Value enableMetricsDashboardtrueUpgrade the Helm charts.
helm upgrade -n axiomatics-asm asm -f asmcharts/values.yaml asmchartsThis starts ASM with InfluxDB and with the Dashboard functionality enabled.
Cloud installation
The steps below apply to cloud installations using EKSOpens in a new tab by Amazon Web Services (AWS).
- Create an IAM policy and roleOpens in a new tab using `eksctl`.
- Install the Amazon EFS driverOpens in a new tab using Helm.
- Create two EFS file systemsOpens in a new tab, for `influx-data` and `influx-config`, in the VPC that EKS is running.
Find the security group of the EKS cluster.
Select EKS cluster > Networking > Cluster security group
Use the same security group for the two EFS file systems you created previously.
Select EFS > select the File System > Network > Manage
Open the
kubernetes/asmcharts/values.yamlfile and set the following:Parameter Value enableMetricsDashboardtrueefsPvInfluxDataVolumeIdThe influx-dataEFS file system ID.
You can find the ID in the EFS console.efsPvInfluxConfigVolumeIdThe influx-configEFS files system ID.
You can find the ID in the EFS console.Upgrade the Helm charts.
helm upgrade -n axiomatics-asm asm -f asmcharts/values.yaml asmcharts
This starts ASM with InfluxDB and with the Dashboard functionality enabled.
Enable cluster-level logging
By default, ASM uses node-level logging where all service containers send their logs to standard output (stdout). The pod logs are temporarily stored in the pod's node and are retained on container restarts but are evicted on pod restarts.
To overcome this limitation, you can enable cluster-level logging on a Kubernetes (k8s) cluster. This type of logging is independent of nodes and pods lifecycle and it requires a separate backend to store, analyze, and query the logs. The logs are collected from all the pods and sent to a separate service.
In case you don't have an ELK environment running, follow the instructions in Elastic documentationOpens in a new tab to create one locally, using Docker.
Create a k8s secret with the Elasticsearch credentials.
ImportantReplace
<LOG_ANALYTICS_USERNAME>and<LOG_ANALYTICS_PASSWORD>with your credentials.kubectl create secret generic elasticsearch-credentials \
--from-literal=username=<LOG_ANALYTICS_USERNAME> \
--from-literal=password=<LOG_ANALYTICS_PASSWORD> \
--namespace kube-systemOpen the
kubernetes/asmcharts/values.yamlfile and set the following:Parameter Value enableFluentdElasticsearchLoggingtrueclusterLogging.hostThe host of the Elasticsearch service.
In case of a local k8s installation, usehost.docker.internal.clusterLogging.portThe port for the logging service.
The default port for Elasticsearch is9200.clusterLogging.schemehttpsUpgrade the Helm charts.
helm upgrade -n axiomatics-asm asm -f asmcharts/values.yaml asmcharts
Configure Policy Designer
Policy Designer offers you the following options:
- Select which Identity Provider (IdP) will be used to allow users to log in
- Apply your own branding to its interface
- Docker deployment
- Kubernetes deployment
Open the
docker/docker-compose.ymlfile and set the following:Add the alias of the IdP to be used by Policy Designer
This is required only if you will be using Policy Designer.
Parameter Value PD_IDP_NAMEThe alias of the IdP that will be configured later in Keycloak to work with Policy Designer. Learn more about the Policy Designer Keycloak configuration.
The default is"google". Other available options:
User-defined
- OpenID Connect v1.0: Make sure that you use the same alias both here and in Keycloak!
- Keycloak OpenID Connect: Make sure that you use the same alias both here and in Keycloak!
Social
- GitHub:"github"
- Facebook:"facebook"
- LinkedIn:"linkedin"
- Instagram:"instagram"
- Microsoft:"microsoft"
- BitBucket:"bitbucket"
- Twitter:"twitter"
- Openshift v4: Make sure that you use the same alias both here and in Keycloak!
- Openshift v3: Make sure that you use the same alias both here and in Keycloak!
- GitLab:"gitlab"
- StackOverfIow:"stackoverflow"
Note: SAML is not supported.
Important: The value should be in lowercase and enclosed in double quotation marks.
Important: The IdP cannot be changed after the installation process is complete.Apply your branding to Policy Designer
Optionally, if you want to apply your own branding to the Policy Designer interface, you should also set the following:
Parameter Value PD_LOGOThe path to the logo image file displayed in the upper left corner of the Policy Designer interface.
The default is"./assets/logo.svg"and the file contains the Axiomatics logo.
Important: If changed, the value should be a valid URL pointing to a JPG/JPEG, PNG, or SVG file. It is recommended that the resolution of the image file is 210x50 pixels.PD_APP_NAMEThe app name/title displayed next to the logo and on the browser window.
The default is"Policy designer".
Important: The limit is 100 characters.PD_MAIN_COLORThe main color used in the Policy Designer interface, for buttons and highlighted components.
The default is"#0274C1".
Important: Replacement colors should be in hexadecimal notationOpens in a new tab.PD_BACKGROUND_COLORThe background color used in the Policy Designer interface.
The default is"#F2F5F8".
Important: Replacement colors should be in hexadecimal notationOpens in a new tab.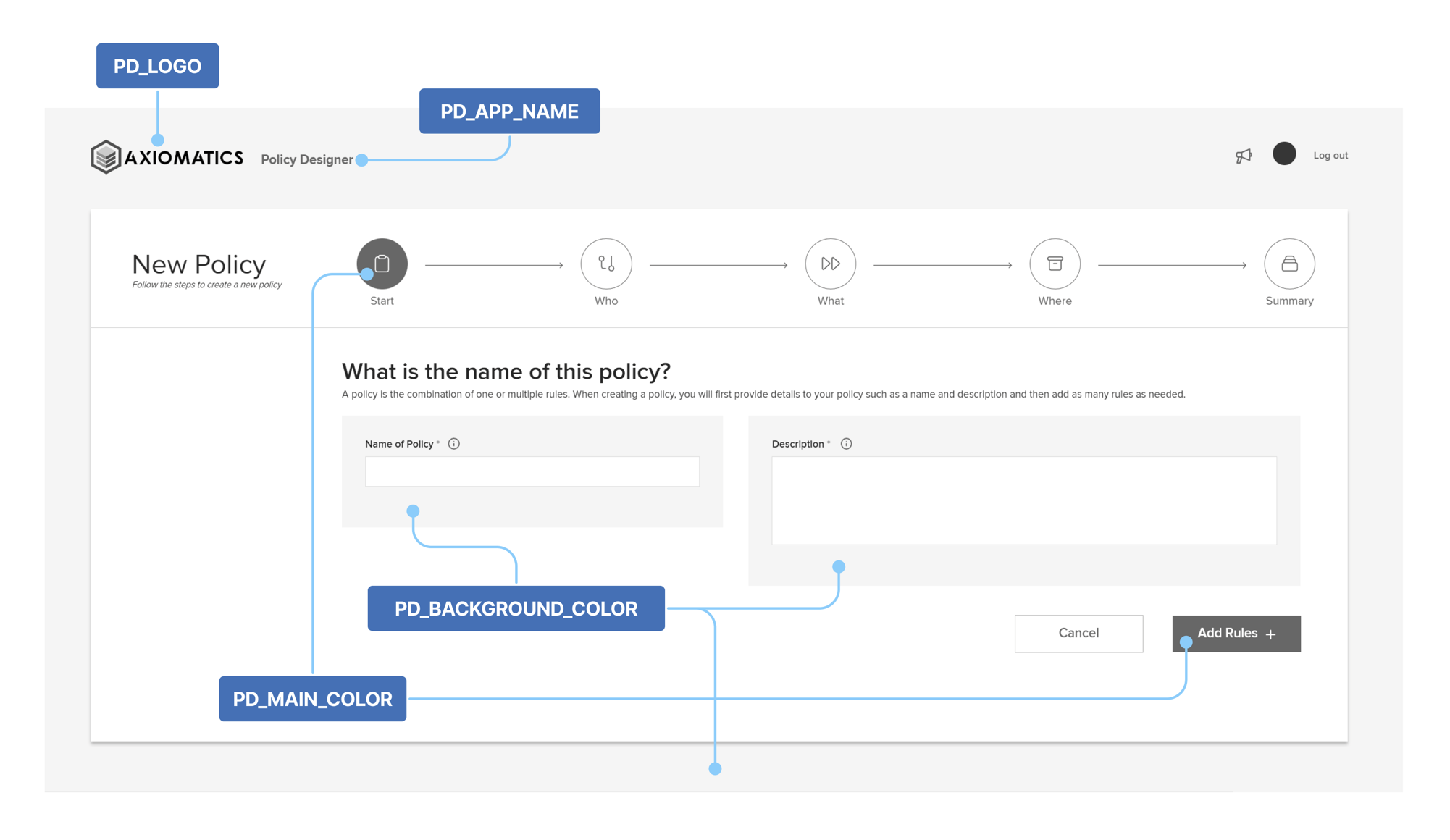
Run the following commands
docker-compose stop pd-uidocker-compose rm pd-uidocker-compose up pd-ui -d
Your configuration is now applied to Policy Designer.
Open the
asmcharts/values.yamlfile and set the following:Add the alias of the IdP to be used by Policy Designer
This is required only if you will be using Policy Designer.
ImportantThe values below are enclosed in both single and double quotes. Make sure to keep both quote types when editing a value. For example,
'"new_value"'.Parameter Value pdIdpNameThe alias of the IdP that will be configured later in Keycloak to work with Policy Designer. Learn more about the Policy Designer Keycloak configuration.
The default is'"google"'. Other available options:
User-defined
- OpenID Connect v1.0: Make sure that you use the same alias both here and in Keycloak!
- Keycloak OpenID Connect: Make sure that you use the same alias both here and in Keycloak!
Social
- GitHub:'"github"'
- Facebook:'"facebook"'
- LinkedIn:'"linkedin"'
- Instagram:'"instagram"'
- Microsoft:'"microsoft"'
- BitBucket:'"bitbucket"'
- Twitter:'"twitter"'
- Openshift v4: Make sure that you use the same alias both here and in Keycloak!
- Openshift v3: Make sure that you use the same alias both here and in Keycloak!
- GitLab:'"gitlab"'
- StackOverfIow:'"stackoverflow"'
Note: SAML is not supported.
Important: The value should be in lowercase and enclosed in double quotation marks.
Important: The IdP cannot be changed after the installation process is complete.Apply your branding to Policy Designer
Optionally, if you want to apply your own branding to the Policy Designer interface, you should also set the following:
ImportantThe values below are enclosed in both single and double quotes. Make sure to keep both quote types when editing a value. For example,
'"new_value"'.Parameter Value pdLogoThe path to the logo image file displayed in the upper left corner of the Policy Designer interface.
The default is'"./assets/logo.svg"'and the file contains the Axiomatics logo.
Important: If changed, the value should be a valid URL pointing to a JPG/JPEG, PNG, or SVG file. It is recommended that the resolution of the image file is 210x50 pixels.pdAppNameThe app name/title displayed next to the logo and on the browser window.
The default is'"Policy designer"'.
Important: The limit is 100 characters.pdMainColorThe main color used in the Policy Designer interface, for buttons and highlighted components.
The default is'"#0274C1"'.
Important: Replacement colors should be in hexadecimal notationOpens in a new tab.pdBackgroundColorThe background color used in the Policy Designer interface.
The default is'"#F2F5F8"'.
Important: Replacement colors should be in hexadecimal notationOpens in a new tab.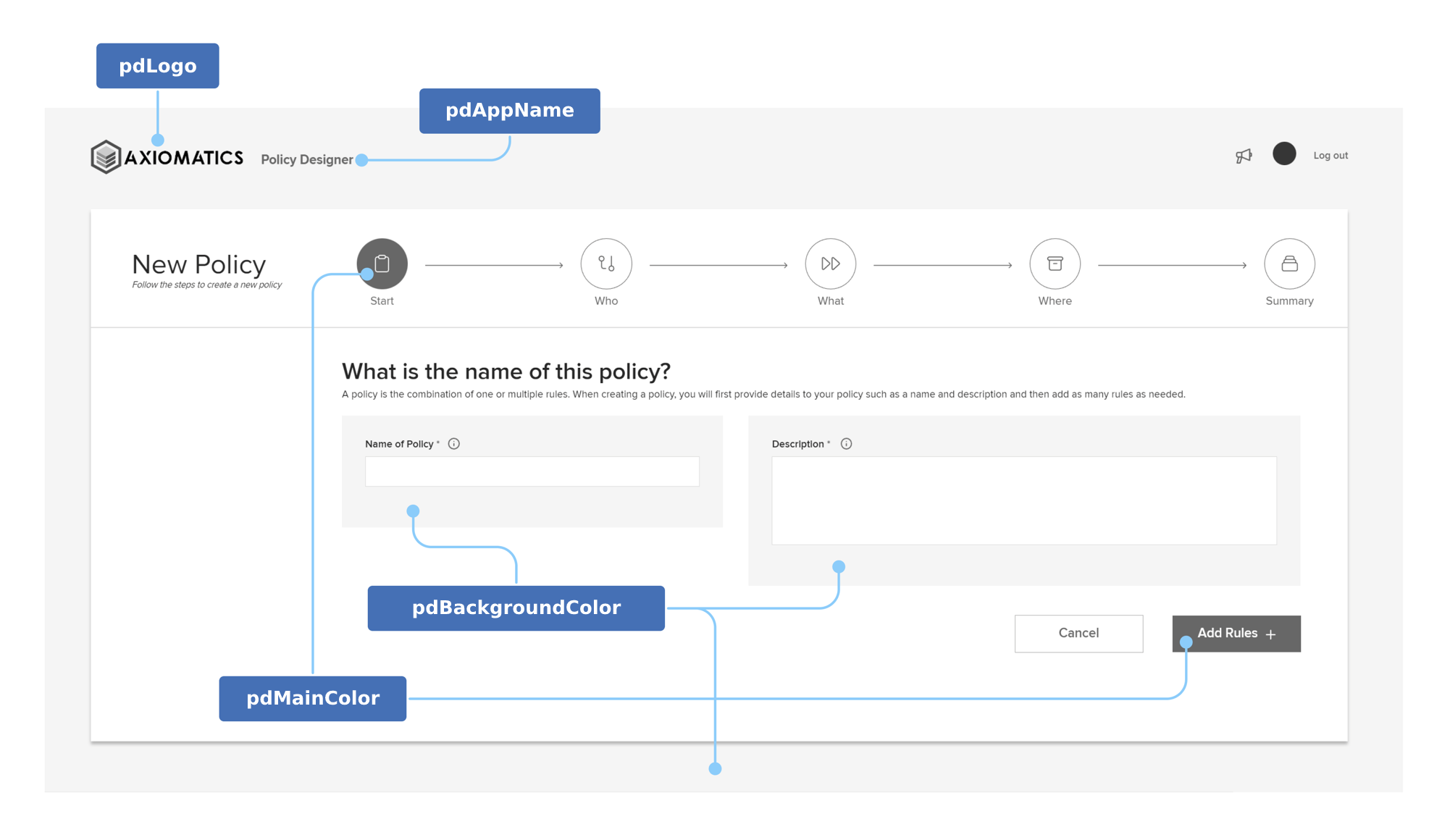
Run the following command
helm upgrade -n axiomatics-asm asm -f asmcharts/values.yaml asmcharts
Your configuration is now applied to Policy Designer.
Update Attribute Connectors
ASM is installed with a default set of standard Attribute Connectors. However, the Attribute Connectors are developed, maintained, and released independently of releases of ASM. New and updated versions may be released and made available for download at any time.
Contact Axiomatics Customer SupportOpens in a new tab for information on latest versions and available downloads.
Standard Attribute Connector versions
This release of ASM is delivered with the following versions of the standard Attribute Connectors:
- LDAP Attribute Connector 6.3.0
- SQL Attribute Connector 6.2.2
- Table Attribute Connector 7.0.0
- HTTP Attribute Connector 5.0.0
- Parser Attribute Connectors 1.0.0
Earlier versions of the Attribute Connectors, with the exception of HTTP and Parser, should be considered incompatible with this version of ASM and should not be used. Updated versions of the Attribute Connectors may be released, which may be installed and used with this version of ASM subject to compatibility information for each attribute connector, respectively.
LDAP Attribute Connector
The LDAP Attribute Connector is used for connection to LDAP data sources. It is already deployed and does not need further installation.
SQL and Table Attribute Connectors
The SQL Attribute Connector and the Table Attribute Connector are both used for connections to SQL data sources. The functionality of the Table Attribute Connector is slightly more restrictive than the SQL Attribute Connector, but it is easier to configure. For more information about the differences between the attribute connectors, read the Attribute Connectors section.
Only the JDBC connection type is supported for the SQL Attribute Connector and the Table Attribute Connectors.
HTTP Attribute Connector
The HTTP Attribute Connector can be used to connect to a web service (HTTP-based service which returns structured content e.g. JSON and XML) and retrieve its payload which it then returns to the PDP.
Parser Attribute Connectors
Some attribute values needed to evaluate authorization policies may be nested in strings formatted following some structured document conventions, such as JSON or XML. Parser Attribute Connectors can take a string in a structured format and extract nested values from it. The choice of values to extract is made using standard means for each format.
The Parser Attribute Connectors consist of the following:
- JSON Parser
- XML Parser
- JWT Parser
Update Standard Attribute Connectors
If an updated version of an Attribute Connector is released, you can check against what is already installed and decide whether an update is required.
If you have updated one or more Attribute Connectors in the past:
- Navigate to the
/docker/asm.core/attribute.connectors/folder where the .jar file(s) used for the update reside. - Identify the Attribute Connector versions from the filename(s).
- Navigate to the
Otherwise, you are using the default Attribute Connectors.
tipThe default Attribute Connectors bundled with each ASM version are listed in the ASM Release Notes.
Refer to the documentation accompanying each Attribute Connector for more information on changes and functional updates in new releases.
The commands for the update are different depending on whether ASM is running with the Dashboard functionality enabled or not.
Update the Attribute Connector(s) with the Dashboard functionality enabled
Extract the contents of the downloaded attribute connector distribution file(s) in the file system and locate the Attribute Connector jar file(s). (See the included documentation for more information.)
Stop ASM if it is running. In the console, navigate to the
docker/folder and run the commanddocker-compose -f docker-compose.yml -f docker-compose.dashboard.yml stopIn a second file system window, navigate to
<root path>/docker/asm.core/attribute.connectors/.There you will find a folder for each of the Standard Attribute connectors, plus one for custom Attribute Connectors.
Copy the updated Attribute Connector .jar file(s) to the relevant folder(s).
For example, the
sql-attribute-connector-<version>.jarwould go into the<root path>/docker/asm.core/attribute.connectors/sql-attribute-connectorfolder, etc.From the
docker/folder in the console, run the commanddocker-compose -f docker-compose.yml -f docker-compose.dashboard.yml build --no-cache asmThis will rebuild the Docker image that contains the attribute connectors.
Also from the
docker/folder, run the commanddocker-compose -f docker-compose.yml -f docker-compose.dashboard.yml upThis restarts ASM, which will now use the new Attribute Connector(s), and the Dashboard functionality is enabled.
Update the Attribute Connector(s) with the Dashboard functionality disabled
Extract the contents of the downloaded attribute connector distribution file(s) in the file system and locate the attribute connector jar file(s). (See the included documentation for more information.)
Stop ASM if it is running. Navigate to the
docker/folder and run the commanddocker-compose stopIn a second file system window, navigate to
<root path>/docker/asm.core/attribute.connectors/There you will find a folder for each of the standard attribute connectors, plus one for custom attribute connectors.
Copy the updated attribute connector .jar file(s) to the relevant folder(s).
For example, the
sql-attribute-connector-<version>.jarwould go into the<root path>/docker/asm.core/attribute.connectors/sql-attribute-connectorfolder, etc.From the
docker/folder in the console, run the commanddocker-compose build --no-cache asmThis will rebuild the Docker image that contains the Attribute Connectors.
Finally, also from the
docker/folder, run the commanddocker-compose upThis restarts ASM, which will now use the new Attribute Connector(s).
The attribute connectors can be updated individually. If an Attribute Connector folder under docker/asm.core/attribute.connectors/ is empty, the deployed ASM will continue to use the Attribute Connector that was included in the release. The folder custom-attribute-connectors is rescanned on every start to reflect the folder content.
Custom Attribute Connectors
When a custom Attribute Finder has been set up on the PDP (Policy Decision Point) side, the same Attribute Finder package must be made available to ASM as an attribute connector so that it shows up in the list of available Attribute Connector types that can be chosen in the ASM GUI.
Attribute Finders are built for the Java ServiceLoader.
Legacy Attribute Finders created for the JSPF plugin framework are supported for use with the current release, but Axiomatics strongly recommends converting them to the Java ServiceLoader mechanism.
Add a Java ServiceLoader Attribute Finder
An Attribute Finder built for the Java ServiceLoader can be plugged into the ASM system by following these steps:
Stop ASM if it is running. Navigate to the
docker/folder and run the commanddocker-compose stopNavigate to
<root path>/docker/asm.core/attribute.connectors/custom-attribute-connectorsCopy the the Attribute Finder (that is, the custom attribute connector .jar file) to this folder.
Restart ASM with the Dashboard functionality either enabled or disabled, as described above.