LDAP Attribute Connector
The LDAP Attribute Connector represents all the information an Authorization Service needs to fetch attributes from an LDAP directory.
Familiarity with LDAP and the ability to write LDAP search expressions are needed to properly configure an LDAP Attribute Connector.
The configuration process has two parts:
A general part specifying the client implementation to use, the location of the LDAP directory, and the authentication mechanism and account to use.
An attribute specific part that specifies which XACML attribute can be fetched and how to obtain it from the directory.
General configuration
Click the "Configuration" link in the Attribute Connector editor to open the base form for the chosen attribute connector type.
| Field | Description | Supported format |
|---|---|---|
| Factory Initial | The value of this property is the fully qualified class name of the factory class that creates the initial context for the LDAP service provider in the Service's LDAP Attribute Finder. | A fully qualified class name. Use the value "com.sun.jndi.ldap.LdapCtxFactory" to select the Oracle/Sun JRE LDAP provider. |
| Provider URL | The LDAP URL that PDPs use to connect to the LDAP Attribute Source. LDAP URLs are typically specified as ldap://<host>:<port> (plaintext) or ldaps://<host>:<port> (secured by TLS), where \<port> normally is 389 for plaintext and 636 for LDAP over TLS. | This field must contain a unique URL address using the character set defined in RFC 1738 ([A-Z][a-z][0-9] and the special characters '-', '_', ':', ';', '?', '%', '&', ';', '=', '#', '\', '.', '/', '+', '"', '<', '>') to a maximum length of 255 characters. |
| Authentication | The type of authentication the PDP should use when connecting to the attribute source. Supported are LDAP bind and no authentication. | One of two: “simple” (LDAP bind) “none” |
| Principal | This field contains the name of the LDAP principal that is used for LDAP authentication. This field becomes enabled if "simple" authentication has been selected. | The name of an LDAP account |
| Password | The password for the LDAP principal selected for the "simple" authentication method. |
The Check connection button
The Check connection button makes it possible to verify the LDAP server connection. Once the Factory Initial and Provider URL have been entered in the ASM UI and the authentication type has been selected, the Check connection button becomes enabled, allowing the user to verify the connection to the LDAP server.
Note: If an LDAP URL has been specified, ASM must have the appropriate chains of CA certificates in order to verify the host certificate in the JSSE trust store ("javax.net.ssl.trustStore").
Attribute-specific configuration
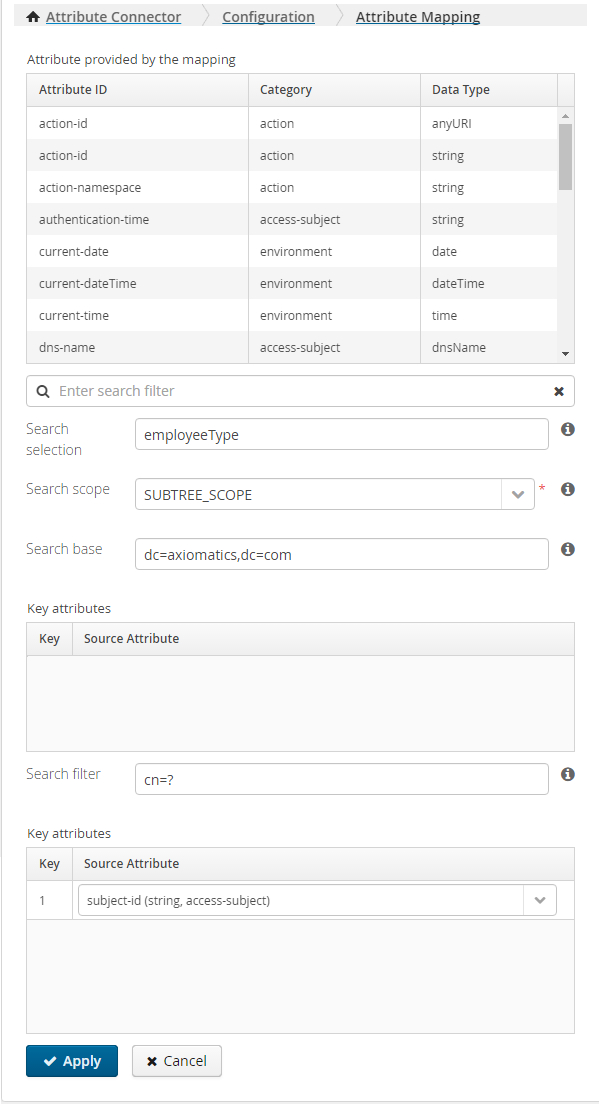
Click the Add button at the bottom of the Attribute Connector editor. This switches to the Attribute Mapping page, where the attribute-specific configuration is managed.
| Field | Description | Supported format |
|---|---|---|
| Attribute provided by the mapping | The URI of the XACML attribute to be fetched from this attribute source. | Selection is done from the list of attributes defined in the Attribute Dictionary. |
| Search selection | The name of the target LDAP attribute that will return the value of the mapped XACML attribute. | LDAP attribute name |
| Search base | The base in the LDAP directory tree from which the search filter will be applied. The search base can be static (i.e. a fixed node) or dynamic in which case it will depend on attribute values in the request. A dynamic search base is created by inserting one or more question marks ("?") in the search base DN. Each question mark is substituted for the value of a specified XACML attribute. See the "Dynamic search base" section for more details. | A valid LDAP-distinguished name with optional question marks ("?") used to denote attribute value substitution when a dynamic search base is used. |
| Search scope | Three search scopes can be specified: OBJECT_SCOPE - This value is used to indicate searching only the entry at the base DN, resulting in only that entry being returned. ONELEVEL SCOPE- This value is used to indicate searching all entries one level under the base DN, but not including the base DN and not including any entries under that one level under the base DN. SUBTREE_SCOPE - This value is used to indicate searching all entries at all levels under and including the specified base DN. | One of "OBJECT_SCOPE", "ONELEVEL_SCOPE" and "SUBTREE_SCOPE" |
| Search filter | The LDAP attribute and value that is used to filter the result set. The values of the key that are used in the query are denoted by a "?" symbol and need to be mapped to an XACML attribute later in the following table. | See the section on search filters below. |
| Cache | A Cache Configuration telling PDPs using the attribute connector configuration how to cache attribute values fetched using the search filter. | See Attribute Cache Configurations for more information. |
LDAP search filters
To search for the value of a target attribute, the Attribute Connector will in most cases need to make use of the value of other attributes from the specific request context. These attributes can be made available either in the request itself or by another search. These "runtime" values filter the full result set into the specific value of the target attribute. For example, an LDAP search can look for a username in the directory given the "userid" value.
Two steps are required to define a supplement attribute as a desired filter for an LDAP search:
Define the LDAP attribute to be used as a the LDAP filter attribute
Map the defined LDAP attribute (called "KEY" in ASM terminology) to the corresponding source XACML attribute that will have to be made available in the specific request context. This is done by selecting the XACML attribute from the combo box next to each filter LDAP attribute defined in the previous step
The LDAP filter is specified using the following syntax:
LDAP-attribute=?
For instance in our previous example with username and userid the definition would look like this:
userid=?
Map the defined LDAP attribute (called "KEY" in ASM terminology) to the corresponding source XACML attribute, which will have to be made available in the specific request context. This is done by selecting the XACML attribute from the combo box next to each filter LDAP attribute defined in the previous step. (See the figure below.)
Key values
An attribute passed to the LDAP Attribute Finder in runtime as a key to lookup another attribute can either contain no key value (an empty set), a single key value, or multiple key values. In cases where
No key value is given -- the Attribute Finder will return an empty set
A single key value is given -- the Attribute Finder runs the query and returns the retrieved data
Multiple key values are given -- the Attribute Finder runs the query multiple times, iterating over the set of key values and collects the full set of all the values returned for each query
Dynamic search base
A dynamic search base is an LDAP search base that can change depending on the value of one or more XACML attributes from the request context or from any configured attribute that can be fetched by means of an Attribute Finder.
A dynamic search base is constructed by inserting one or more question marks ("?") in the DN string wherever substitution for an attribute value is needed. As soon as a question mark is entered in the search base string, a corresponding key mapping field is added in the search base key associations table.
An XACML attribute has to be selected for each question mark.