Creating a new domain
- To create a new domain, go to the Domain Management page and click the Create new Domain button on the right-hand side of the page.
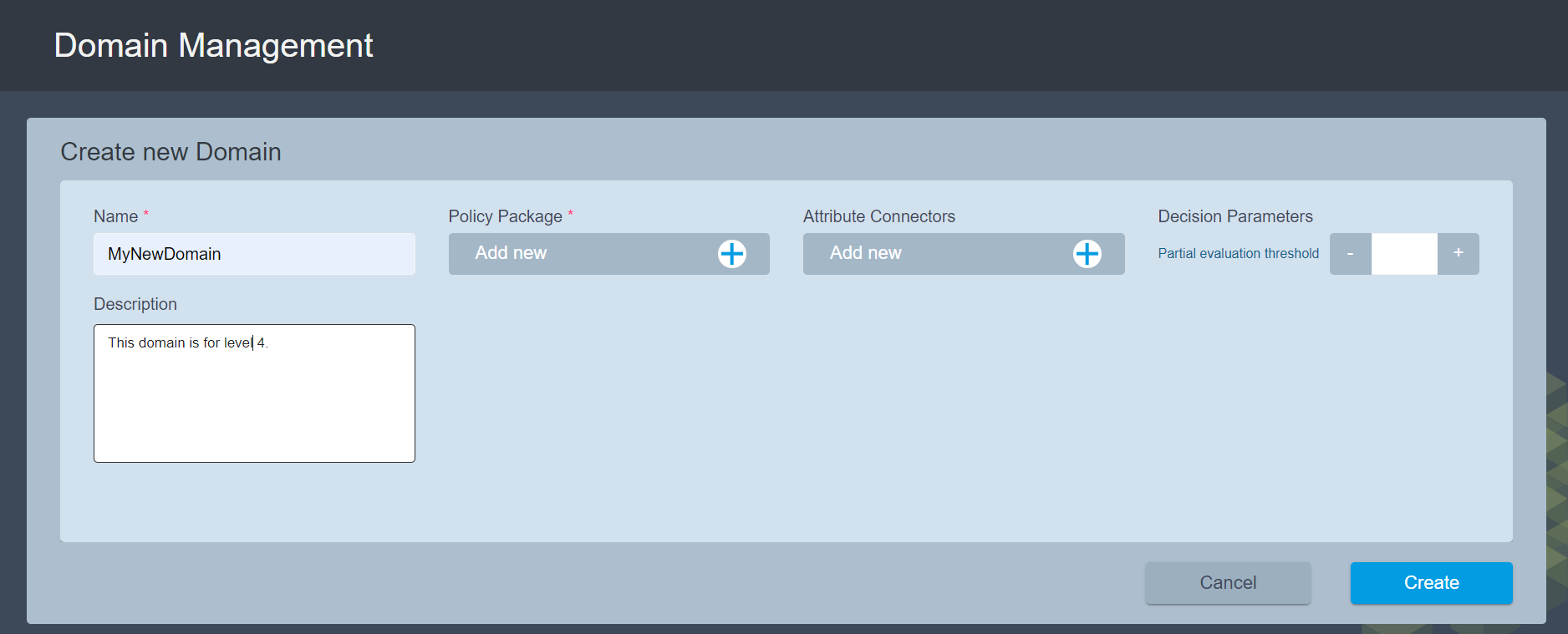
An empty Domain Editor page is displayed where you can specify the domain configuration.
Enter and/or select the required information and then click the Create button in the lower right-hand corner of the page to finish.
Domain configuration
Domains have a set of general settings needed for deployment and configuration:
Name (required)
Enter a name for the new domain. The name is used to refer to the domain within the Axiomatics Services Manager GUI.
Important: The length of a domain name is limited to 500 characters.
Description
This is an optional field where you can provide more details about a domain.
Policy Package
A Policy Package is a data structure that contains XACML policies and/or policy sets that can be assigned to a domain. A policy package is a required component of the domain.
- Click the Add new button under the Policy Package heading.
A dialog box is displayed with a list of available policies in the Policy Package Library. The list is searchable.
- Click to put the insertion point in the search field and start typing.
It is a dynamic search; for every character you type, the list of potential policy packages gets shorter.
- Click a policy package in the list to select it.
- Click Save to add it to the domain.
Note: The simplest possible domain configuration requires only a Policy Package. The absence of Attribute Connectors implies that all attribute references in the Policy Package are provided by the Policy Enforcement Point (PEP).
Creating a Policy Package
Any software tool, including plain text editors, with which you can produce XACML 3.0 compliant policies can be used to create policy packages.
There are three tools provided by Axiomatics that you can use to create policies: the Policy Editor within ASM, the Policy Administration Point (PAP), and the Axiomatics Language for Authorization (ALFA) plugin and compiler.
Policies created in the Policy Editor are automatically added to the library. Policies created with external tools must be imported to the library to become available for selection. See Import a Policy Package for more information.
Note: If changes are made to a policy package in the Policy Editor, these changes are not automatically transferred to the domain. To update the policies in the domain, select the policy package again to reload it with the latest version.
Attribute Connectors
A domain can be configured with zero or more attribute connectors. An attribute connector is required when attributes used in a policy need to get their values from an external source such as a database or an LDAP directory. A source of such data is called a Policy Information Point (PIP). The authorization engine connects to a PIP via an attribute connector.
The attribute connector contains information about the type of attribute source (for example, LDAP, or SQL), the XACML attributes it provides, and how to obtain them (query strings specific to the PIP type and instance). The attribute connectors themselves are then used at runtime during policy evaluation.
Adding attribute connectors
- Click the the Add new button under the Attribute Connectors heading.
A dialog box is displayed with a list of the available attribute connectors. The list is searchable.
- Click to put the insertion point in the search field and start typing.
It is a dynamic search; for every character you type, the list of potential attribute connectors gets shorter. (See Attribute Connector Management for more information about attribute connectors.)
- Click an item in the list to select it.
More than one attribute connector can be selected. Click again on a selected item to deselect it.
- Click Save to add the selected attribute connector(s) to the domain.
Each attribute connector is represented in the panel. Scroll the list of attribute connectors if necessary.
Note: If changes are made to an attribute connector configuration in the Attribute Connectors section, these changes are not automatically transferred to the domain. To update the attribute connector in the domain, select it again to reload it with the latest configuration.
Decision parameters
This optional property controls how the authorization engine should attempt to perform multiple-request optimization. In some cases this can improve the performance of authorization engine. In some special cases it may have a negative impact on performance. The actual improvement depends on several factors, for example, the structure of the request and the structure of the policy.
Enabling this property means that the authorization engine will attempt to perform multiple-request optimization.
The threshold value indicates how many individual requests a multiple-decision request should contain before the authorization engine attempts to optimize that specific multiple request.
This setting is enabled by entering a value in the Partial Evaluation Threshold field in the Decision parameters block. You can enter a value directly or click the plus or minus buttons to set a value.
If enabled, two requirements apply:
the value must be an integer
the value must be between 2 and 9999 (the values 0 and 1 are not allowed)
If the threshold value is set too low, it may reduce performance. If the threshold value is set too high, it is less likely that it will be reached. The correct number cannot be determined without testing.