Authentication
Authentication using an authorization server
ADS can be configured to authenticate itself against Axiomatics Services Manager (ASM) or any authorization server, and send client credentials when requesting a domain configuration file from an authorization server.
To configure this, you must add the property authHttpClientConfiguration to the deployment configuration file.
authHttpClientConfiguration:
clientId: ads
clientSecret: <String>
tokenUri: https://<hostname>/auth/realms/asm/protocol/openid-connect/token
timeout: 5 seconds
Authorization server configuration
Axiomatics recommends using environment variables to populate sensitive information, for example.
authHttpClientConfiguration:
clientId: ${AUTH_SERVER_CLIENT_ID}
clientSecret: ${AUTH_SERVER_CLIENT_SECRET}
tokenUri: ${AUTH_SERVER_TOKEN_URI}
timeout: 5 seconds
Authorization server configuration using environment variables
- Open the deployment configuration file in a text editor.
- Add the property
authHttpClientConfiguration: - Add the parameters
clientId:,clientSecret:,tokenUri:, andtimeout:
These are the parameter values to set:
clientId: A valid String which should be the name of the client (configured in the authorization server), that is, the ADS instance name.
clientSecret: A valid String which is the generated secret for the specific client (configured in the authorization server). It is automatically generated after the clientId has been configured.
tokenUri: A valid URL which is the specific URI to the authorization server:
noteThese three parameters and their values must be configured in the authorization server in question before they are entered/copied into the deployment configuration file.
timeout: The maximum idle time for a connection, once established. The recommended starting value is 5 seconds. The default value is 500 ms.
TLS options
TLS can be configured in different ways, to accommodate the requirements of your implementation.
TLS
authHttpClientConfiguration:
clientId: ${AUTH_SERVER_CLIENT_ID}
clientSecret: ${AUTH_SERVER_CLIENT_SECRET}
tokenUri: ${AUTH_SERVER_TOKEN_URI}
timeout: 5 seconds
tls:
keyStorePath: file:<path_to_file>/client.keystore
keyStorePassword: changeit
keyStoreType: pkcs12
TLS with client certificate
authHttpClientConfiguration:
clientId: ${AUTH_SERVER_CLIENT_ID}
clientSecret: ${AUTH_SERVER_CLIENT_SECRET}
tokenUri: ${AUTH_SERVER_TOKEN_URI}
timeout: 5 seconds
tls:
keyStorePath: file:<path_to_file>/client.keystore
keyStorePassword: changeit
keyStoreType: pkcs12
trustStorePath: file:<path_to_file>/client.truststore
trustStorePassword: changeit
trustStoreType: pkcs12
Authorization server configuration with TLS and TLS with client certificate
Concurrent use with httpClientConfiguration
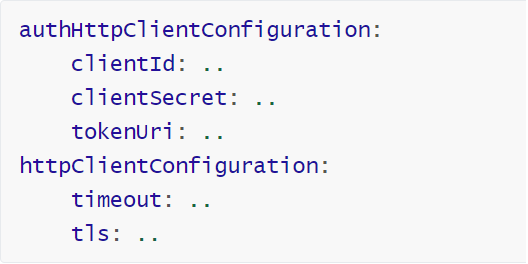
The configuration authHttpClientConfiguration can be set concurrently with the httpClientConfiguration (see below). However, some restrictions apply.
Configure ADS to retrieve authorization domain from ASM
ADS can be configured to retrieve its authorization domain from ASM/ADM or a standalone ADM. To do so, you can configure the domain property of the deployment.yaml file in order to retrieve the domain using one of the two ADM’s endpoints as displayed in the examples below:
To retrieve the domain from ASM, you have to configure the authentication to ASM as described in Concurrent use with authHttpClientConfiguration section.
ADS using RetrieveDomainByName endpoint
The RetrieveDomainByName endpoint is used to retrieve a specific domain within a namespace.
Example:
domain: https://<hostname>/adm/api/namespaces/test/names/testA/domain
In this example test is the namespace and testA is the domain name.
ADS using RetrieveDomainByID endpoint
The RetrieveDomainByID endpoint is used to retrieve a specific domain instance by its id.
Example:
domain: http://<hostname>/adm/api/domains/e8a9e7d6-8fc6-4706-ac7d-a74eff74c58c
In this example e8a9e7d6-8fc6-4706-ac7d-a74eff74c58c is the domain-id.
HTTP client configuration
To have ADS send user credentials when requesting a domain configuration file from remote locations that support Basic Authentication, you need to configure the httpClientConfiguration property in the deployment configuration file.
httpClientConfiguration:
domainUser: ${HTTPCLIENT_USER}
domainPassword: ${HTTPCLIENT_PASS}
timeout: 5 seconds
HTTP client configuration
- Open the deployment configuration file in a text editor.
- Add the property
httpClientConfiguration: - Add the parameters
domainUser:,domainPassword: - Add the property
timeout:
There are four values to set:
- domainUser: The user name.
- domainPassword: The password of the user.
- timeout: The maximum idle time for a connection, once established. The recommended starting value is 5 seconds. The default value is 500 ms.
Axiomatics recommends using environment variables to populate the sensitive information when configuring the user/password required by the server where the domain is located.
If you want ADS to read the domain configuration from a file on the local file system, then the httpClientConfiguration property is not needed.
TLS options
TLS can be configured in different ways, to accommodate the requirements of your implementation.
TLS
httpClientConfiguration:
domainUser: ${HTTPCLIENT_USER}
domainPassword: ${HTTPCLIENT_PASS}
timeout: 5 seconds
tls:
keyStorePath: file:<path_to_file>/client.keystore
keyStorePassword: changeit
keyStoreType: pkcs12
TLS with client certificate
httpClientConfiguration:
domainUser: ${HTTPCLIENT_USER}
domainPassword: ${HTTPCLIENT_PASS}
timeout: 5 seconds
tls:
keyStorePath: file:<path_to_file>/client.keystore
keyStorePassword: changeit
keyStoreType: pkcs12
trustStorePath: file:<path_to_file>/client.truststore
trustStorePassword: changeit
trustStoreType: pkcs12
HTTP client configuration with TLS and TLS with client certificate
Concurrent use with authHttpClientConfiguration
The configuration httpClientConfiguration can be set concurrently with the authHttpClientConfiguration (see above). However, when the authHttpClientConfiguration is used, the httpClientConfiguration cannot include the domain properties.
This configuration is allowed This configuration is NOT ALLOWED
Authentication using self-signed certificates
ADS can be configured to trust self-signed certificates. This option can be enabled or disabled via the deployment.yaml file by changing the trustSelfSignedCertificates property as displayed in the examples below.
The trustSelfSignedCertificates property is disabled by default.
Due to security-related risks, Axiomatics does not recommend the use of the self-signed certificates configuration for production environments.
ADS using self-signed certificates with authHttpClientConfiguration
authHttpClientConfiguration:
tls:
trustSelfSignedCertificates: true
ADS using self-signed certificates with httpClientConfiguration
httpClientConfiguration:
tls:
trustSelfSignedCertificates: true